-
Weird Web Series: Packing Data onto Your Browser

Welcome back to Post #2 of this Weird Web series. For those who found their way here outside of my LinkedIn, the idea is to explore unconventional (and occasionally rebellious) ways to use the internet. In this ‘episode’ we’re examining how most browsers provide (free) data storage and sync mechanisms – that you can exploit…
-
Weird Web Series: A Dynamic Website on S3?

During covid (as all good stories start) a good friend and I got very into making cocktails together over Facetime. We called it ‘Booze-day Tuesdays‘, later simply Tuesdays. If we ever open a cocktail bar, that’s its name. Though, we quickly realised that tracking our mixology journey wasn’t a job for pen and paper… and…
-
3D Printing Perfectly Imperfect Jenga
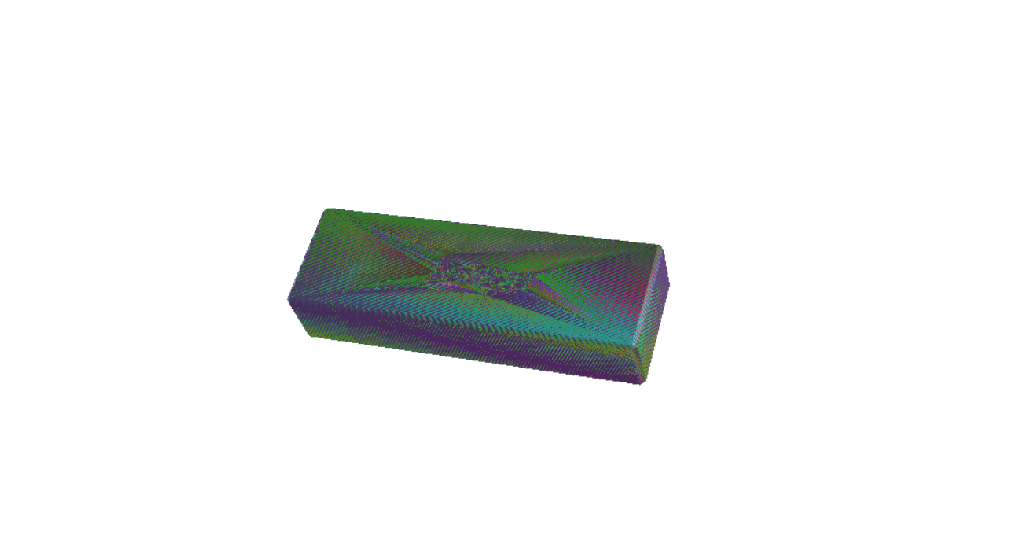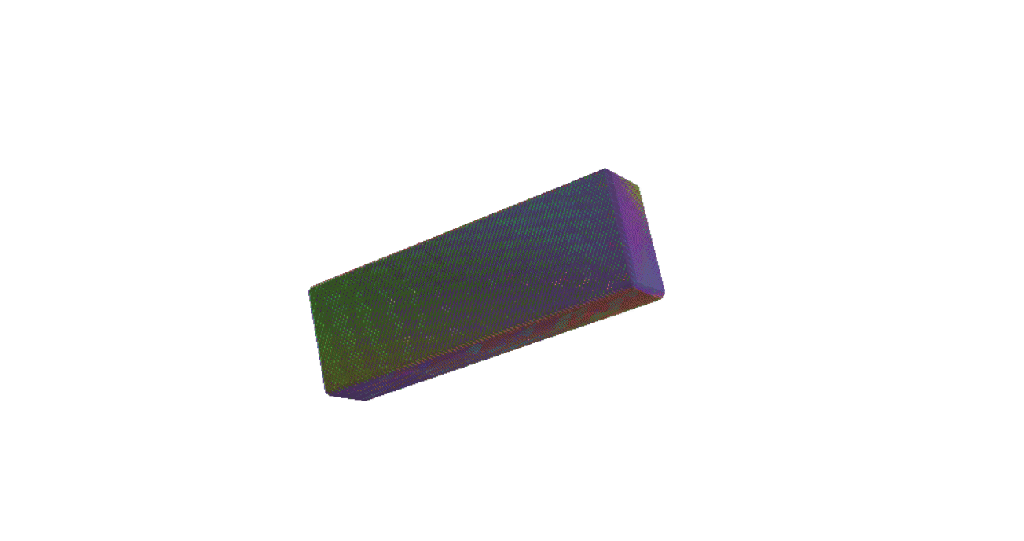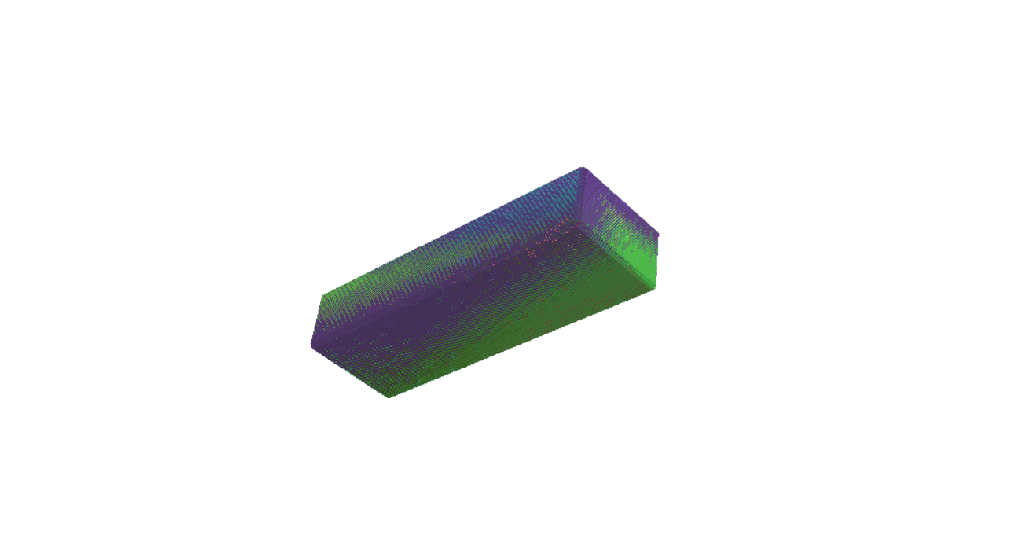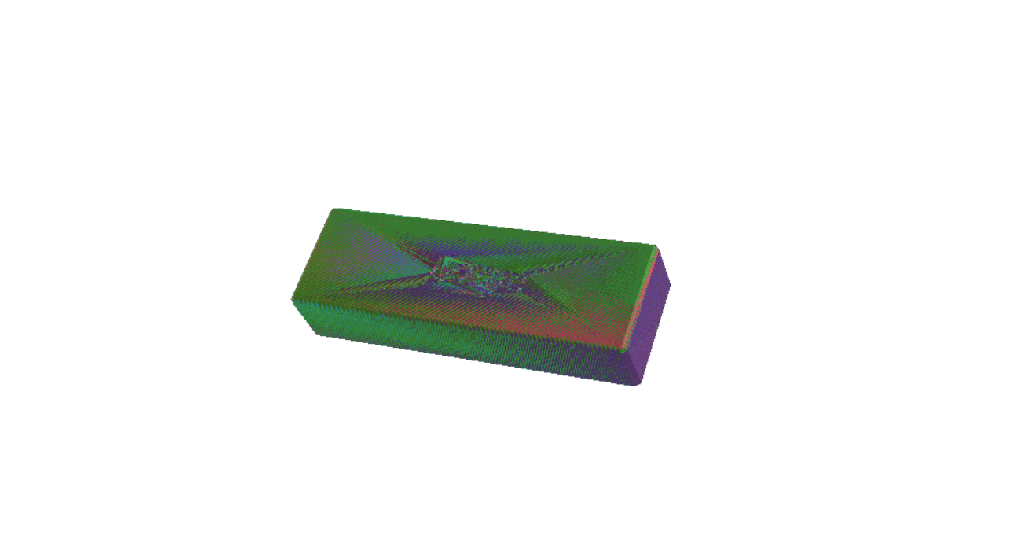
Today I watched an old Ted talk by the creator of Jenga – Leslie Scott. At 8 minutes 45 seconds in, she states that “Crucially, the wooden blocks are not identical. The game just wouldn’t work if they were. In fact, each of the wooden blocks in a Jenga set is very slightly different to…
-
The Witness in Vanilla JS
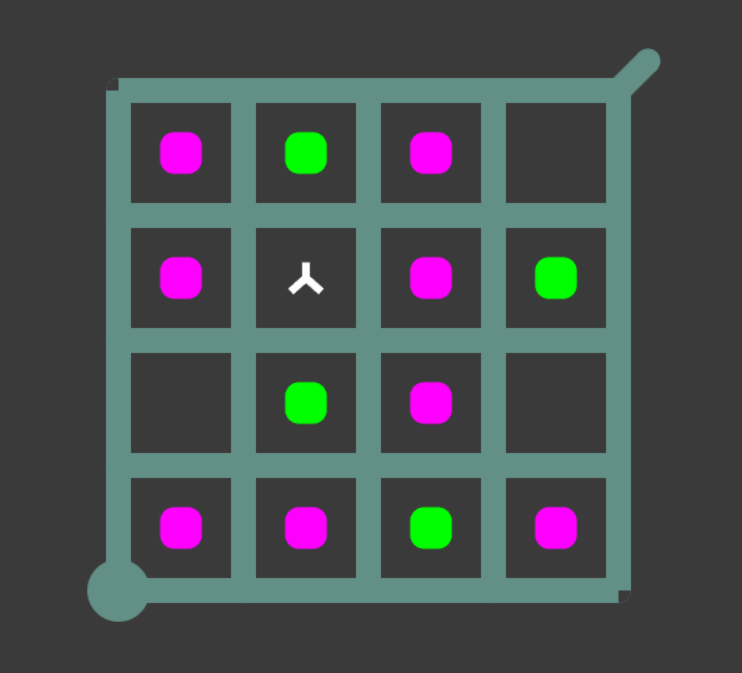
I love puzzle games. At some point in the last 6 months i stumbled on a puzzle game on called The Witness. Its not a new game, so this isn’t a review… but what i will say… is that the puzzle mechanics led to some of the most satisfying puzzles i’ve experienced in a game.…
-
Guided Access Mode Bypass
As a penetration tester who specialises in mobile apps, I get good visibility of how the enterprise is adopting/using/misusing various iOS capabilities and MDM features. One trend I’ve seen increasingly, is the use of ‘Guided Access Mode‘ to lock down devices. Guided-Access Mode (GAM), for the unfamiliar, locks the device into a single app. It’s…
-
High Performance Web Brute-Forcing 🕸🐏
Finding and exploiting unique attacks on web applications is, of-course, satisfying. But I also find that performing the most basic of attacks, but as efficiently and effectively as possible, can also pose a decent mental challenge that’s equally rewarding. In this short post i’ll show you how writing just a few lines of code can…
-
Kinda LIKE SQL Injection
TLDR: This post is about some late 90’s level hacking. But the fact is, that there just doesn’t exist a decent explanation of this vulnerability anywhere on the internet.. and yesterday, in 2018, I found another application vulnerable to it (to quite serious effect). I’m afraid that was the straw that broke the camel’s back.…
-
Much Badoo About Nothing
This is just a short post about toying with the Badoo app for iOS, but also touches on something ever-so-slightly useful about testing the app-upgrade mechanisms of mobile apps. “Urghh more dating app hacking” I hear you say. I know, I know, this is getting old. At some point i’ll get a real hobby, I promise.
-
‘App Forgery’
In this (pretty long) post, I’m going to attempt to coin a name for an application vulnerability, most commonly found in mobile apps. This is “App Forgery”.
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.